 In our recent report, “The Governance of Telecommunications Surveillance: How Opaque and Unaccountable Practices and Policies Threaten Canadians,” we discussed how the Communications Security Establishment (CSE) developed and deployed a sensor network within domestic and foreign telecommunications networks. While our report highlighted some of the concerns linked to this EONBLUE sensor network, including the dangers of secretly extending government surveillance capacity without any public debate about the extensions, as well as how EONBLUE or other CSE programs programs collect information about Canadians’ communications, we did not engage in a comparison of how Canada and its closest allies monitor domestic network traffic. This post briefly describes the EONBLUE sensor program, what may be equivalent domestic programs in the United States, and the questions that emerge from contrasting what we know about the Canadian and American sensor networks.
In our recent report, “The Governance of Telecommunications Surveillance: How Opaque and Unaccountable Practices and Policies Threaten Canadians,” we discussed how the Communications Security Establishment (CSE) developed and deployed a sensor network within domestic and foreign telecommunications networks. While our report highlighted some of the concerns linked to this EONBLUE sensor network, including the dangers of secretly extending government surveillance capacity without any public debate about the extensions, as well as how EONBLUE or other CSE programs programs collect information about Canadians’ communications, we did not engage in a comparison of how Canada and its closest allies monitor domestic network traffic. This post briefly describes the EONBLUE sensor program, what may be equivalent domestic programs in the United States, and the questions that emerge from contrasting what we know about the Canadian and American sensor networks.
What is EONBLUE?
EONBLUE was developed and deployed by the CSE. The CSE is Canada’s premier signals intelligence agency. The EONBLUE sensor network “is a passive SIGINT system that was used to collect ‘full-take’ data, as well as conduct signature and anomaly based detections on network traffic.” Prior Snowden documents showcased plans to integrate EONBLUE into government networks; the network has already been integrated into private companies’ networks. Figure one outlines the different ‘shades of blue’, or variations of the EONBLUE sensors:
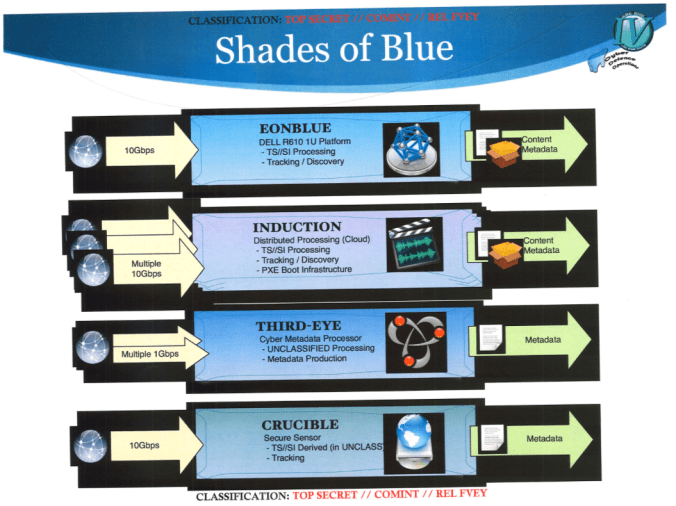
The CSE sensor network is composed of a set of interrelated network appliances; INDUCTION has similar capabilities as EONBLUE, and has been deployed domestically at the gateways between domestic and international network domains: CSE documents state that the agency had “100% INDUCTION coverage of main SSO sites + metadata production.” This placement lets the CSE monitor all traffic coming into, and exiting, Canadian Internet space. Other appliances that were deployed include a metadata production and processing program, THIRD-EYE, which operated at selected new sites and an unclassified sensor which was designed to track targets and be deployed in non-highly secured locations (i.e. not in Sensitive Compartmentalized Information Facilities).
Using EONBLUE, the Canadian intelligence agency “hoped to detect threats before they entered national infrastructure, to identify exfiltration and command and control systems, and transform the network itself into a defensive domain. This final objective would require CSE to be able to change data traffic routes, silently discard packets, and insert payloads into data packets. CSE regarded such expansive ‘defensive’ activities as necessary because gateway or end-node defence was insufficient to protect government systems.” The EONBLUE network is used to detect and mitigate threats, such as from state-sponsored hackers, and is part of the CSE’s attempts to conduct ‘dynamic defence’ operations. Such operations involve placing sensors “in the core of the global internet to act on, and modify, data traffic, as well as implanting malware on foreign infrastructure to probe, explore, and learn about adversary network space and gather information and tools used by adversaries. These ‘defensive’ operations may be supplemented with influencing technology, such as anti-virus companies’ signatures, developing relationships with supply chains, or political maneuvers. Such activities are segregated in the ‘Cyber Activity Spectrum’ from active operations and deception techniques.”
The decision logic, which is used to generate alerts that malicious activity may have been detected by the EONBLUE sensors, is shared between the American, Canadian, British, Australian, and New Zealand signals intelligence agencies since 2009 or 2010. While this served the goal of facilitating cross-national defence there were later proposals that it could also be used for intelligence collection during discussions about building out the EONBLUE network. Regardless, there was historically a sharing of the logics, and presumably signatures, that the aforementioned intelligence agencies used to detect and respond to potential malicious threats.
In summary, EONBLUE is a globally deployed sensor network that includes installations in Canadian networks. It is part of the CSE’s efforts to detect and respond to potential threats and, also, acts based on information that is shared between closely allied signals intelligence agencies. EONBLUE fundamentally operates as a frontline analyzer of data traffic that can act upon (and modify) data traffic based on policies loaded into its component sensors.
The NSA Equivalent(s) to EONBLUE?
On June 4, 2015, the New York Times (NYT) reported on the domestic American sensor network that the National Security Agency (NSA) had developed and deployed. The NSA network may — and likely does — have parallel capabilities as EONBLUE. The NYT report was based on documents provided to journalists by Edward Snowden, and paper revealed that in mid-2012 a set of memos were penned by Department of Justice lawyers that authorized the NSA to monitor for addresses and signatures that could be tied to hacking attempts on domestic US networks. According to the NYT, the documents do not make it clear “what standards the agency is using to select targets.”
Per the documents, the NSA sought permission to copy data that was exfiltrated from US government and corporate networks in the course of monitoring the activities of foreign-based hackers. NSA officials wrote that:1
many cyber threat targets currently cannot be tasked to [FISA Amendments Act Section 702] FAA702 due to lack of attribution to a foreign government or terrorist organization. The new certification will not require this attribution, and rather only require that a selector be tied to malicious cyber activity. The FAA702 collection will then be used to determine attribution, as well as perform collection against known targets.
The NSA documents do not provide a comprehensive example of all types of signatures that would be monitored for by the agency’s sensors; the signatures would include “IP addresses, strings of computer code, and similar non-email or phone number-based selectors.” The NSA would monitor for these signatures at Special Source Operations (SSO) locations. In this use, SSO refers to companies that have integrated these NSA sensors into their infrastructures and, in the case of the documents discussed by the NYT, include American telecommunications companies.
Based on the NYT reporting and the documents themselves, we know that the NSA expected to capture large volumes of data associated with digital signatures. As an actor used malware or other technique to extract data, both the signature and presumably related data (e.g. registering it was malware type X and copying data relevant to the malware’s technical operation) along with exfiltrated data was identified by the NSA sensors and subsequently sent to a database for additional analysis. Lawyers advising the NSA warned that any exfiltrated data — which was taken from US government agencies or US-based companies — that was stored would likely to contain significant volumes of American citizens’ data. The rationale for collecting this large volume of personal information was to identify the likely actor(s) behind an attack. By analyzing the full volume of exfiltrated data clues about who was responsible, or why that data set was targeted, might become apparent.
NSA lawyers noted that ‘incidentally’ collecting American persons’ data in this way was a valid kind of collection. However, speaking notes that accompanied a training document read:2
[b]ecause this type of exfiltrated data potentially can contain so much [United States Person] information, [the Office of General Council] advises that this type of exfiltrated data be segregated from the rest of the [signals intelligence] raw traffic and is made availabe only to those who have the mission to collect/report on these types of foreign intrusions. The exfiltrated data does not contain any [foreign intelligence] other than what is reported in order to understand what the foreign hacker was seeking, and what the foreign hacker obtained for damage assessments.
It remains unclear whether this advice was adopted by NSA analysts in practice, as well as whether the same guidance would be given today based on the contemporary state of US law, the Department of Justice’s and Office of the General Council’s present interpretations of law, or relevant changes to US government policies.
Domestic Agency Access to NSA Sensors
A 2012 memo that the NYT reported on stated that “over the last decade, NSA has expended a significant amount of resources to create collection/processing capabilities at many of the chokepoints operated by U.S. providers through which international communications enter and leave the United States.” The same memo discussed how the FBI, using its own warranted permission to intercept telecommunications traffic, could utilize the NSA’s existent domestic surveillance capacities. Cost was the primary rationale for authorizing the FBI to access the NSA’s signals intelligence infrastructure: the FBI would “have to reimburse the providers to recreate (i.e., duplicate) what NSA has already put in place. The cost alone would be prohibitive, and the time lost in doing so would necessarily result in a loss of foreign intelligence.”
Perhaps most surprising is the degree of autonomy given to SSOs in determining whether the FBI should enjoy access to the NSA’s Commercial Off The Shelf (COTS) sensors. SSOs “will make careful and informed decisions” prior to letting the FBI use COTS that “involve components developed at NSA’s expense and used, primarily, for NSA’s Cyber survey purposes.” There is no suggestion in the memo that the FBI would receive access to the NSA’s Government Off The Shelf (GOTS) intelligence collection and processing infrastructures which have been deployed into American telecommunications companies’ networks. The document does, however, indicate a higher than previously assumed level of corporate responsibility for facilitating government surveillance: in deciding whether to authorize use of NSA equipment SSOs are transformed from receiving an order to conduct domestically-warranted interceptions into actors who are involved in negotiating the mechanisms for interception in order to defer costs and inconveniences to law enforcement organizations.
Whither EINSTEIN 3?
Separate reporting by Bloomberg about the recent exfiltration of sensitive US government personnel files highlighted the failings of the perimeter security infrastructure that has been established within major telecommunications networks. The infrastructure, known as EINSTEIN 3, is:
designed to stop attacks before they reach government computers. The five major Internet service providers — Verizon Communications Inc., AT&T Inc., Sprint Corp., Level 3 Communications Inc. and CenturyLink Inc. — use it to sniff the huge volume of data moving to and from sensitive networks and then use digital signatures to spot and delete hackers’ tools.
While the Bloomberg article discusses conflicts between the Department of Defence, Department of Homeland Security, and other federal agencies as delaying the deployment of EINSTEIN 3 it fails to note the NSA’s role in the newest version of the domestically-situated sensor network. Though dated, Wired noted in 2009 that:
telecommunication companies would route data going to and from government networks through an NSA monitoring box, which would examine the traffic for malicious code or suspicious activity suggestive of a network attack.
Wired‘s reporting has been supplemented by research conducted by Susan Landau who, in her book Surveillance or Security: The Risks Posed by New Wiretapping Technologies, found that:
Einstein 3 represented a major change. Einstein 2 monitors communications at the federal network access points. In Einstein 3, agency-bound traffic is diverted to an intrusion-prevention system. The communications are searched using NSA tools and hardware. Traffic matching known or suspected malware will be blocked … Einstein 3 differs from its predecessors in that it is designed to check packet content in addition to transactional information.
Privacy concerns were prominent even in 2009, with the then-Secretary of the Department of Homeland Security asserting that the NSA’s technical resources “will be guided, led and in a sense directed by the people we have at the Department of Homeland Security.” It is not clear whether the EINSTEIN 3 system is linked to the sensor networks mentioned in the NYT article though, if not, then sensor networks with parallel capacities and purposes have been established by the NSA within major US-based telecommunications infrastructures.
Conclusion
It isn’t immediately apparent how the four ‘types’ of EONBLUE sensors (i.e. EONBLUE, INDUCTION, THIRD-EYE, and CRUCIBLE) directly contrast against the NSA’s COTS and GOTS sensor systems. Nor is it clear whether particular types the EONBLUE system, or the NSA’s COTs and GOTs systems, have a direct parallel with the EINSTEIN 3 sensor network. What is clear, however, is that the NSA must be analyzing traffic using an equivalent of the EONBLUE system.
We know that CSE and the NSA have, in the past, shared threat information with one another so that data collected and parsed by sensors such as EONBLUE could be rapidly interrogated using shared decision logics. No Snowden documents have clarified the extent to which these shared logics are automatically integrated into non-Canadian sensor systems; thus, while it is possible that information generated by Canadians for EONBLUE are subsequently integrated into EINSTEIN 3, as well as the COTS and GOTS systems, and vice versa, we lack the documents that would positively confirm this hypothesis or clarify the rapidity at which decision logics are integrated into the parters’ sensor systems.
The NYT article sheds light on how the NSA and FBI interoperate and use the same sensors. There is no evidence in the Canadian-based Snowden documents that CSIS or other Canadian federal agencies enjoy the same degree of access to EONBLUE sensor systems as the FBI does to NSA sensors. However, memorandums of understanding have shown that CSIS and CSE are deeply interoperated with one another and we know that CSIS can obtain warrants (under Section 16 of the CSIS Act) that are then fulfilled using CSE equipment: just as the FBI requires a warrant before it can task network sensors built for the NSA, CSIS requires a warrant before CSE’s systems can be activated to track specific persons for Canadian Security Intelligence Service.
Ultimately, then, while the NYT article and accompanying Snowden documents reveal more about how telecommunications traffic is monitored and analyzed, we are left primarily with better-informed questions as opposed to answers concerning the sharing of rules or logics that trigger domestic sensor networks to collect domestically-originated data, whether EINSTEIN is linked with the COTS and GOTS systems referenced, or whether CSIS and the FBI enjoy similar access to sensors their respective signals intelligence agency has embedded in domestic telecommunications infrastructure. Nevertheless, even the limited transparency afforded by the latest tranche of documents is helpful in advancing our understand contemporary domestic and foreign intelligence operations that target domestic telecommunications traffic. And the secrecy with which these sensors have been deployed continue to emphasize the need for governments to be more transparent about how they monitor telecommunications traffic, why, and what is done with the monitored information.
NOTE: This post first appeared at the Telecom Transparency Project website.
Project Support

Research for the report, “The Governance of Telecommunications Surveillance: How Opaque and Unaccountable Practices and Policies Threaten Canadians,”was funded through the Canadian Internet Registration Authority’s .CA Community Investment Program. Through the Community Investment Program, .CA funds projects that demonstrate the capacity to improve the Internet for all Canadians. The .CA team manages Canada’s country code top-level domain on behalf of all Canadians. A Member-driven organization, .CA represents the interests of Canada’s Internet community internationally.
Footnotes
- Note: the FISA Amendments Act Section 702 permitted the Attorney General and Director of National Intelligence to jointly authorize the targeting of person believed to be located outside of the United States, but is limited to targeted non-U.S. persons. ↩
- We have modified the text to replace acronyms (e.g. USP) with the complete term (e.g. United States Person) to help readers understand this piece of quoted material. ↩